Researchers uncovered a security weakness in three different WordPress plugins that affect over 84,000 websites and might be used by a malicious actor to take control of them.
In a report released last week, Wordfence, a WordPress security company, noted.
“This flaw allowed an attacker to change arbitrary site settings on a susceptible site if they could trick the site’s administrator into completing an action, such as clicking on a link.”
The cross-site request forgery (CSRF) bug, dubbed CVE-2022-0215, is scored 8.8 on the CVSS scale and affects three Xootix plugins —
- Login/Signup Popup (Inline Form + Woocommerce),
- Side Cart Woocommerce (Ajax), and
- Waitlist Woocommerce (Back in stock notifier)
Cross-site request forging, also known as one-click attack or session riding.
It occurs when an authorized end-user is tricked into making a specifically designed online request.
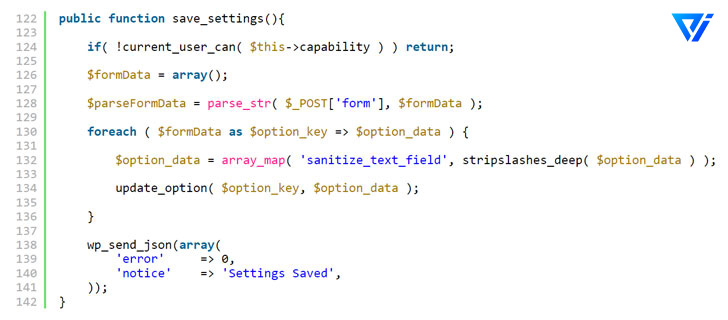
The flaw stems from a lack of validation when processing AJAX requests.
Allowing an attacker to set the “users can register” (i.e., anyone can register) option on a site to true.
And the “default role” option to the administrator (i.e., the default role of users who register on the blog).
Thereby granting them total authority.
Side Cart Woocommerce and Waitlist Woocommerce have over 4,000 and 60,000 installs, respectively, while Login/Signup Popup has over 20,000 installations.
Login/Signup Popup has over 20,000 installations, while Side Cart Woocommerce and Waitlist Woocommerce have over 4,000 and 60,000 installations, respectively.
After responsible disclosure by Wordfence researchers in November 2021.
The bug was resolved in Login/Signup Popup version 2.3, Side Cart Woocommerce version 2.1, and Waitlist Woocommerce version 2.5.2.
The discoveries came just over a month after hackers used flaws in four plugins and 15 Epsilon Framework themes to assault 1.6 million WordPress sites as part of a large-scale attack effort that spanned 16,000 IP addresses.
Though this Cross-Site Request Forgery (CSRF) vulnerability is less likely to be abused due to the need for administrator input, it may have a major impact on a successfully attacked site.
Conclusion
As a result, as such, it serves as an incredibly important reminder to remain aware when clicking on links or attachments and to ensure that your plugins and themes are regularly updated.